This is an old revision of the document!
- slackware
- Jonathan Haack
- Haack's Networking
- netcmnd@jonathanhaack.com
First, let's install Slackware using full disk encryption using Luks, along with LVM. This is based on the Grey Seeker tutorial, and is the officially supported full disk encryption as documented here Slackware Encryption. First, lets create our partitions using gdisk:
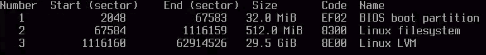
gdisk /dev/sda <n, enter, enter, +512M, ef02 code for BIOS boot> <n, enter, enter, +2000M, default code for /boot partition> <n, enter, enter, enter, 8e00 code for LVM> <p, to print the configuration of the partitions>
If you did that correctly, it will look like this:
If everything looks good, then execute the following in gdisk:
<w, Y, enter>
Now, it is time to create your crypt using cryptsetup:
cryptsetup luksFormat -c aes-xts-plain64:sha512 -h sha512 -s 256 /dev/sda3 cryptsetup luksOpen /dev/sda3 vault0then
Now, it is time to setup LVM, by first creating the physical volume, and then after that, the logical volume group, and finally the logical volumes:
pvcreate /dev/mapper/vault0 vgcreate slack /dev/mapper/vault0 lvcreate -C y -L 8G -n swap slack lvcreate -C n -L 32G -n root slack lvcreate -C n -l 100%FREE -n home slack
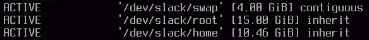
Verify your setup using lvscan. If you set up lvm correctly, it will look like this:
After that, we need to activate and format swap:
mkswap /dev/slack/swap
Now, let's now begin the installation by running setup. Now, use the installer and assign all of the proper partitions for the installer. Begin by adding swap, as that will prompt you to find the others automatically (as opposed to using Target). Once it adds swap, and adds the entry /etc/fstab it is now time, to individually select the lvs created above. First up, select /dev/slack/root for the root partition and then choose the file system ext4. Now, next, let's select the boot partition which is /dev/sda2 and format the file system as ext2 using /boot as the mount point. Lastly, it is time to select the home partition, so in this case, using a fast journaling file system like xfs is preferable and then specify /home as the mount point. Enter continue at the prompt now, and verify that you configured the partiions correctly by comparing the /etc/fstab entry that appears to this:
As long as that all came out okay, now we can proceed with installing Slackware - enter whichever media you used to boot into the live slackware instance, in my case, it was USB. Now, it is time to install packages. I recommend the full installation so you have what you need and can start working. Now, once the OS completes its installation, let's skip the USB bootstick option, and select the “simple” lilo install (it will not install properly, and we will fix it later). Do not pass extra kernel arguments, do defaults on the rest, and then select “install to MBR” when you get to the option to choose where to install the lilo bootloader. Go ahead and configure the network, choose your hostname, etc., and unless you are in need of binding to a domain, enter “local” on the domain entry. Next, you can choose your network configuration. I have found that Slackware's implementation of Network Manager is jenky and fails on many WPA2 networks, so I choose DHCP, and then I use the commands at the beginning of this tutorial for each network I visit with this workstation. You will now be prompted to select services that start at boot, which I leave as default since any of these can be activate later, and unless you know you need one, the UNIX rule is to not run the service. After you select the services, you get to choose the hardware clock time, the default DE. I choose XFCE, and then lastly, you specify the root password, and then press enter to get back the ncurses installer, and lastly select ok, but then do not reboot. You know need to specify a compatible kernel to use with luks and lvm, and then use mkinitrd to activate it, and then lastly edit your lilo.conf, and then unmount the partitions and reboot. Here is how to do that:
mount cd /mnt chroot . /bin/bash -l
Now, make the initrd as follows so the system can recognize the partition. Verify what kernels you have first, however, in case you are using this to do a similar setup on a different release!
ls /boot
Pick the generic kernel - not the “huge” kernel. It is not time to specify your kernel and make your init ram disk as follows (check this carefully, and make sure you understand every flag and parts of the command or you should not run it):
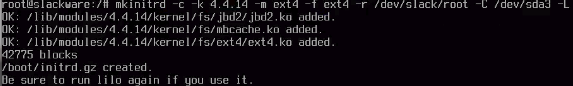
mkinitrd -c -k 4.4.14 -m ext4 -f ext4 -r /dev/slack/root -C /dev/sda3 -L
If you did not run this correctly, you will get quick output that obviously looks wrong. If you did it correctly, you will get this output:
Now, let's maually verify that the command you just ran in fact created the initrd.gz as follows:
cd /boot ls
Look for the file called initrd.gz and if it is there, you are ready to proceed and update and notify the lilo bootloader of the changes we made to the OS regarding which kernel, which initrd, and which file system to use for boot and root. Edit lilo.conf:
nano /etc/lilo.conf
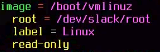
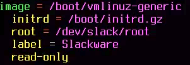
You may optionally uncomment #compact … to speed up the boot time by bypassing the bios check, but the main parts you need to change are the boot configuration at the bottom of the file. Here is how the configuration originally looks:
Here is how it should look after you have adjusted the configuration to reflect the changes you made with mkinitrd. Slackware's luks and lvm requires the generic kernel (not the so-called huge ones), and you also need to introduce the initrd. Now, change the label, as long as it is unique and different from the previous one, giving us something like:
After that, close and save the file and update lilo:
lilo
It has now added our Slackware entry to the bootloader program lilo. You can safely ignore the VESA errors as they are either false positives or you picked an incomatible configuration, regardless, Slackware will default to text and continue to boot. It is now a good idea to exit chroot environment, and to unmount everything in order to sync the buffers to disk:
exit
cd umount -l /mnt reboot [pull out the install media]
Warning: the first boot will hang at Triggering udev events: /sbin/udevadm trigger –action=change for a bit, but wait it out and it will not hang on subsequent reboots. Once it has booted up, let's do some common sense configuring. First, let's add a non-root user:
adduser
Follow the prompts then join wheel group, then add these by using up arrow
wheel,floppy,audio,video,cdrom,plugdev,power,netdev,lp,scanner
Now, log in using the new user, and then run startx if you prefer a graphical environment and a Terminal emulator. Likely, the first thing you will want is WiFi access. To Set up a WPA2 network, proceed as follows:
nano /etc/wpa_supplicant.conf
Make it look like this:
ctrl_interface=/var/run/wpa_supplicant
ctrl_interface_group=0
eapol_version=1
ap_scan=1
fast_reauth=1
network={
scan_ssid=0
ssid="your_essid"
proto=WPA2
key_mgmt=WPA-PSK WPA-EAP
pairwise=CCMP TKIP
group=CCMP TKIP
psk=your_64_hex_characters_long_key
}
To get your psk key, run:
wpa_passphrase ssid 'passphrase'
Then, edit the /etc/rc.d/rc.inet1.conf as follows:
IFNAME[1]="ath0" IPADDR[1]="" NETMASK[1]="" USE_DHCP[1]="yes" DHCP_HOSTNAME[1]="" [leave blank if using more than one SSID, and let wpa_supplicant priority handle] WLAN_WPA[1]="wpa_supplicant" WLAN_WPADRIVER[1]="wext"
Once everything is configured, restart the interface as follows - if everything connects, and you get the nickname error, just ignore it as it will go away on reboot:
/etc/rc.d/rc.inet1 wlan0_restart
Okay, now to add open networks, just add the following to wpa_supplicant:
network={
ssid="sitc"
key_mgmt=NONE
}
Later, I will add how one can use priority = within these configs to cycle through various networks in a specific order, but for now, it is easiest to switch manually as follows:
iwconfig wlan0 essid <nameofssid>
Now that you are online, let's set up sudoer access:
nano /etc/sudoers
Then, add this directly below the root user line that is similar to this:
username ALL=(ALL) ALL
Now, how to update packages:
nano /etc/slackpkg/mirrors
Uncomment one of the mirrors from USA - use http - once that is done:
slackpkg update gpg slackpkg update slackpkg install-new slackpkg upgrade-all slackpkg clean-system
Set up a crypt for sensitive data:
cryptsetup luksFormat /dev/sdaX cryptsetup luksOpen /dev/sdaX vault mkfs.xfs -L vault /dev/mapper/vault mkdir /mnt/vault mount /dev/mapper/vault /mnt/vault
After you reboot and login again, then open the crypt and mount it as follows:
cryptsetup luksOpen /dev/sdaX vault <enter passphrase> mount /dev/mapper/vault /mnt/vault
— oemb1905 2019/06/16 23:48