This is an old revision of the document!
- gnulinux
- Jonathan Haack
- Haack's Networking
- netcmnd@jonathanhaack.com
Welcome to my gnulinux wiki page. This page has simple and complex system administrationnotes to remind me when I forget something that I already learned! If you are visiting, I hope you find the page useful.
#powerpc gnulinux notes; issues, installs +
Making a bootable usb stick …
diskutil list diskutil eraseDisk <filesystemtype> <partitionname> <diskidentifier> diskutil unmountDisk <diskidentifier>
Examples
sudo dd if=/Volumes/Cave/Users/axes/Desktop/lubuntu.iso of=/dev/disk4 bs=1m sudo dd if=/Users/me/tails-i386-1.3.iso of=/dev/rdisk9 bs=16m && sync
Insert USB drive into PPC Mac of choice, depress command-option-o-f (open firmware) try usb0, usb1, usb2, etc. until it works and finds the port you used for the img
probe-usb boot usb0/disk@1:2,\\yaboot boot usb1/disk@1:2,\\yaboot
once inside the yaboot shell, some common examples are:
install url=mintppc.org install cli cli-expert cli64 cli64-expert
#wireless hardware drivers, b43 cutter +
deb http://httpredir.debian.org/debian/ wheezy main contrib non-free deb http://http.debian.net/debian/ jessie main contrib non-free apt-get update sudo lspci apt-get install firmware-b43-installer apt-get install firmware-b43-lpphy-installer apt-get install firmware-b43legacy-installer
use lspci above and then visit https://wiki.debian.org/bcm43xx#supported-b43
#some imaging notes
convert .iso to .img syntax example
hdiutil convert -format UDRW -o destination_file.img source_file.iso diskutil list diskutil partitionDisk /dev/disk1 1 "Free Space" "unused" "100%" dd if=[Directory/to/udrw/img] of=/dev/disk1 bs=1m diskutil eject /dev/disk2
Plug into the Intel Mac, hold option while booting, proceed w/ install
#optical media ripping from command line
cdrecord -pad -dao -data blag-140k-i686.iso
#security & policy information
sudo nano /etc/pam.d/common-password
Prevent Log in - create file
/etc/nologin
tcpdump common uses; monitoring traffic on network
tcpdump -n -i <eth0> <host> <x.x.x.x> tcpdump -n -i <eth0> <port> <#> tcpdump -i eth0 -nn -c 10 tcp and host <x.x.x.x> tcpdump -i wlan0 port http or port smtp or port imap or port pop3 -l -A | egrep -e 'pass=|pwd=|log=|login=|user=|username=|pw=|passw=|passwd=|password=|pass:|user:|username:|password:|login:pass |user |Referer:'
Generate
sudo htpasswd -c .htpasswd username
Syntax for .htaccess
AuthUserFile /private/etc/httpd/.htpasswd AuthGroupFile /dev/null AuthName "Members Only" AuthType Basic
<Limit GET POST> require valid-user </Limit>
#display managers; lightdm & gdm3
cd /usr/share/lightdm/light.conf.d/
Global lightdm settings here
cd /etc/lightdm/ sudo nano lightdm.conf
Lightdm ubuntu-MATE greeter and lock screen issues
/usr/share/common/backgrounds/ubuntu-mate-common/Ubuntu-Mate-Cold.jpg /etc/lightdm/lightdm-gtk-greeter.conf
The .conf file w/ some common sense parameters
[SeatDefaults] allow-guest=false greeter-hide-users=true
#ubuntu-MATE; DE 'porting' and tweaks 2 OS
sudo apt install mate-tweak cd /etc/apt/sources.list sudo nano sources.list <add contrib non-free to default debian repositories> sudo apt update sudo apt upgrade sudo reboot <upon reboot, begin the harvesting of ubuntu-MATE themes> cd /etc/apt/sources.list sudo nano sources.list <in the config file you just opened add the two repos below - no braces!> <deb http://us.archive.ubuntu.com/ubuntu yakkety main restricted non-free> <deb http://us.archive.ubuntu.com/ubuntu yakkety universe main restricted non-free> sudo apt update sudo apt install ubuntu-keyring-archive sudo apt update sudo apt install ubuntu-mate* <computer might crash during install, reboot, repeat or remove wildcard and install piecemeal> sudo apt autoremove cd /etc/apt/sources.list sudo nano sources.list <change the config file and comment out ubuntu repositories> <#deb http://us.archive.ubuntu.com/ubuntu yakkety main restricted non-free> <#deb http://us.archive.ubuntu.com/ubuntu yakkety universe main restricted non-free> sudo apt update sudo apt autoremove sudo apt update sudo apt upgrade sudo reboot <there could / will be problems when you attempt to sudo apt update - if so> sudo apt update --fix-missing <may need to run with and without ubuntu repos> sudo dpkg --reconfigure -a <there may also be a file in var that needs removed - be careful> rm -rf /var/<path/to/locked/file/from/apt/update/on/ubuntu>
#mac - hardware - gnulinux requirements
mac fan control; needed to ensure computer does not fry …
apt-get update apt-get install macfanctld /etc/macfanctl.conf <set desired values> service macfanctld restart
#openWRT Notes
First, we need a router to set up openWRT on. This tutorial uses the WNDR3800. I set it up with openWRT as follows:
Download the image for openWRT. I used the following site:
https://downloads.openwrt.org/chaos_calmer/15.05.1/ar71xx/generic/openwrt-15.05.1-ar71xx-generic-wndr3800-squashfs-factory.img
Get on the proper subnet, and stop the network-manager from hijacking connection. Run `ip a` to obtain your interface name, as it may not be eth0.
sudo systemctl stop network-manager ip a a 192.168.1.105/24 dev eth0
Put a paperclip in the reset button while device is off. Keeping it in, turn the device on, wait for flashing green. First, ping the router.
ping 192.168.1.1
If you cannot successfully ping the router, then re-add your interface to the proper sub net and try again. If you can, then the curl command below should work. Wait for the router to reboot after running the curl command.
curl -T ~/Downloads/openwrt-15.05.1-ar71xx-generic-wndr3800-squashfs-factory.img tftp://192.168.1.1
Now that we have openWRT on the router, we should enable https for the web admin panel. First, verify that you completed the above steps correctly by visiting `192.168.1.1` in your web browser of choice.
opkg update opkg install luci-ssl nano /etc/config/uhttpd
In the config file, comment out the port 80 lines to prohibit using the router with https. Additionally, enter the parameters for the self-signed cert using the options at the bottom of the configuration file. Once you are done, restart the service and build the cert.
/etc/init.d/uhttpd restart
Now that we have https, we can begin to set up the vpn server on the WNDR. Using the template files in the directory openvpnconfig, migrating them over to the router for ease. If you would like this template, email me at netcmnd@jonathanhaack.com. This is, of course, optional. If you would like to view the default templates, rename the original files with `mv` before executing the commands below.
scp -r openvpnconfig root@[openwrt]:/etc/config/ ssh root@[openwrt]
Simplified instructions, using the template files in the directory openvpnconfig.
opkg update opkg install zip openvpn-easy-rsa openvpn-openssl
mv /etc/config/openvpnconfig/openvpn /etc/config/ mv /etc/easy-rsa /etc/config/openvpnconfig/ cd /etc/ ln -s config/openvpnconfig/easy-rsa ./ nano /etc/config/openvpnconfig/easy-rsa/vars <source vars> nano /etc/config/openvpnconfig/openvpnWRT.conf nano /etc/config/openvpn
build-ca build-dh <OR> sudo openssl dhparam -out /tmp/dh2048.pem 2048 build-key-server server
Build your keys for testing - the template also includes a script which builds all the necessary client keys for you, and then places them in `/etc/easy-rsa/keys/` in a .zip file for easy migrating and downloading. You can enter the command without parameters to see its syntax.
/etc/config/openvpnconfig/easyrsa-user-setup-openwrt.sh [username] [server.com]
Using the luci web admin page, go to interfaces, add interface, select tun0, and set up fw zone. Using the luci web admin page, go to firewall, traffic rules, and then specify a rule that allows incoming vpn connections on udp 1194 to device.
Test away using the key you made two steps ago!
sudo openvpn location.com.ovpn
Tweak various client config settings and match on server … specify cipher levels and versions as such:
</etc/config/openvpnconfig/nameofvpnserver.conf> tls-version-min 1.2 tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256:TLS-DHE-RSA-WITH-AES- 128-GCM-SHA256 cipher AES-256-CBC
#samba share basics
sudo apt update sudo apt install samba sudo adduser username sudo smbpasswd -a username mkdir /home/username/sharename nano /etc/samba/smb.conf [sharename] path = /home/username/sharename available = yes valid users = camalas read only = no browseable = yes public = yes writable = yes
#sitc
start or stop network manager (or other services)
systemctl <start/stop/restart> networkmanager.service /etc/init.d/network-manager <start/stop/restart>
verify dhcp client working for interface eno1
dhclient -v eno1
add subnet to interface eno1
ip address add 192.1##.1##.2/24 dev eno1
interface tool w/ eno1 example
ethtool eno1
interface with switch using screen
screen /dev/ttyUSB0/ 19200
calculate subnet automatically
subnetcalc
proxying web traffic through remote server
ssh -D <port#> <user>@<domain.com>
get block ID of drives
blkid
nmap example to get addresses of hosts / devices on lan
nmap -sP 10.##.##.0/24
find utils example
find . -iname "<name>"
#git basics
git - force git to use ssh & pull / push to verify
git remote set-url origin git@github.com:oemb1905/haackyard-gh.git git clone ssh://<user>@<##.##.##.##>/home/git . git commit -am"notes inside here" git pull git push
#nano / text editor basics
ctl-r read -open file curr. buffer, or new in multibuffer mode, enter4new empty buffer ctl-o writeout i.e. save file cctl-x exit i.e. quit; also exits from buffer in multibuffer mode; asks writeout/save ctl-g get help/aid/assistance enter, ctl-m newline bksp, ctl-h delete previous character del, ctl-d delete current character left, ctl-b backward character right, ctl-f forward character home, ctl-a beginning of line end, ctl-e end of line up, ctl-p previous line down, ctl-n next line pgup, ctl-y previous page pgdn, ctl-v next page m-space previous word ctl-space next word alt-\ beginning of file alt-/ end of file ctl-c display cursor position ctl-/ go i.e. jump to line and column ctl-^ set/unset mark; or alt-a alt-^ copy marked, or copy line if nomark; actually alt-6 i.e. do not need shift key ctl-k cut marked or cut lineifnomark or cut2end line if cut2end is enabled using alt-k ctl-u paste cut or copied alt-t cut to end of file ctl-w search alt-w search again alt-r search and replace alt-< previous file buffer; actually alt-, i.e. do not need shift key alt-> next file buffer; actually alt-. i.e. do not need shift key alt-x toggle bottom help display alt-y toggle color syntax hiliting;colors config via /usr/share/nano/*.nanorc files alt-c toggle cursor position display alt-d toggle dos/unix format option at writeout/save prompt alt-k toggle cut to end of line ctl-t show file list at read/open prompt ctl-x prompt for external command to execute at read/open prompt and insert output ctl-z suspend to shell; use fg to return
#scripts and miscellaneous
downloading scripts and executing them; example from DO
curl -sSL https://agent.digitalocean.com/install.sh | sh
ngrok notes; private http(s) tunnels
./ngrok http 80 wget https://[ngrok tunnel]/id_rsa.pub cat ~/id_rsa.pub >> ~/.ssh/authorized_keys
query hosts on the lan
avahi-browse -tl _workstation._tcp
Debian print system configuration to stdout; use root
cat /proc/cpuinfo && lspci | grep -i vga && uname -a && lsb_release -a lsb_release -a lspci
Debian repo management
cd /etc/apt nano sources.lsit [main contrib non-free]
Uploading files to remote webservers with sftp
cd ~/Downloads sftp user@host.com:/path/to/sftp/directory/of/choice/ > put /path/to/file.txt
#Building From Source to Custom library Location
tar -xf <source_filename>
Navigate to the directory that tar unarchived the files to. Then, within that directory, execute:
./configure --prefix=/usr/local make sudo make install clean
#Cacti Server Notes
Installing snmpd to an embedded system and then installing cacti to a client to monitor the device. Additionally, this tutorial covers one way to monitor a client without an snmpd server running on the client machine (ping only). The embedded OS is openWRT on a Netgear WNDR.
ssh -p ###### root@nameofembeddedhost opkg update opkg install snmpd cd /etc/config nano snmpd /etc/init.d/snmpd enable /etc/init.d/snmpd restart
There are many customizations possible, but my colleagues recommend the minimum of changing the name of the public community to something indicative of the network purpose. Additionally, it is also adviseable to change three fields below that refer to the physical location, ip address, and the contact email for the system administrator in charge of managing the snmp server. Once you are done, continue to installing cacti on a network machine that will field the incoming snmp request
sudo apt install cacti
I used the default recommendations, however, when cacti failed repeatedly I was forced to use the reconfiguration command below. The OS I used in this case was Debian 9.2.1 Stretch.
sudo dpkg-reconfigure cacti <Yes, rebuild database, default to other options> <I chose matching MySQL pass because it failed with blank>
At this point, cacti should work so to speak, but it will need to be configured and have its license terms accepted. Since cacti utilizes a web server with which users may access its data, users must configure cacti within that interface. FYI - I chose defaults, and used apache2, as follows from within the Firefox web-browser:
localhost/cacti <say yes to EULA, etc.> <user: admin> <pass: admin>
Since cacti's web server is running, its web server page can highlight information from the snmp server that it queries information from as a client (& many other queries too!). I would error on the side of portraying more information, not less, so consider the following configurations from within the web interface.
Device Add #SNMP Server# ucd/net SNMP Host Ping or SNMP ICMP Ping Version 2 <name of public community chosen ^>
During this install I had a conflict with a previously installed web server nginx, so I had to find its process and then kill it:
netstat -enpl sudo kill -XXX PID
After that, I restarted the web-server apache2 as follows:
sudo /etc/init.d/apache2 restart
#Private Git Server
Configure the machine that will be running the git server first. In order, this requires creating the git user, and then creating the .ssh directory and authorized keys files, and then establishing appropriate permissions.
sudo adduser git su - git cd ~ mkdir .ssh && chmod 700 .ssh touch .ssh/authorized_keys && chmod 600 .ssh/authorized_keys
You can add keys to authorized keys file using copy and paste, or using some bash syntax (from within the git user's shell) as follows:
cat /tmp/id_rsa.john.pub >> ~/.ssh/authorized_keys
Now, let's finish configuring the server.
cd /srv mkdir git cd git/ mkdir repositoryname.git cd repositoryname.git/ git init --bare --shared
The shared option above allows more than just the git user to write to the repository. The users must have permissions to do so, however, so since the directories were created by the git user, one can add the user to the git group. If you need this functionality, then on the server, make sure to execute the following command for each user:
sudo adduser <username> git
The instructions below assume the clients are on the same LAN and using a directory in their home directory dedicated to git repos. If the clients are not on the same LAN, then use openvpn to tunnel into the LAN.
cd ~ mkdir git cd git/ git clone git@gitserver:/srv/git/repositoryname.git cd repositoryname/ nano README git commit -am"added a line to README for repository participants" git push origin master
This method has everyone using the user git in order to clone the repository, and unless tweaked will allow users shell access to the server. To stop shell access, simply add :/bin/false to the end of the git user's entry in /etc/passwd.
Using other user names for access / cloning will be covered in a later tutorial.
#Beagle Bone Black w/ Debian
To locate device if auto-mounted
sudo dmesg
umount /dev/mmcblk0p1
Optional: use fdisk to remove the partition first before dding …
sudo dd of=/dev/mmcblk0 if=/home/sexa/Downloads/bone-debian-9.2-iot-armhf-2017-10-10-4gb.img bs=1M conv=fdatasync [or && sync]
After this, pull out SD card. Plug back in. Locate where it mounted, prepare to edit file to allow it to run the installer upon boot. This is located in boot/enV.txt relative to wherever the media mounted. Eg., cd /media/sexa/rootfs/boot/
cmdline=init=/opt/scripts/tools/eMMC/init-eMMC-flasher-v3.sh
Get out of the directory asap. then:
umount /dev/mmcblk0p1
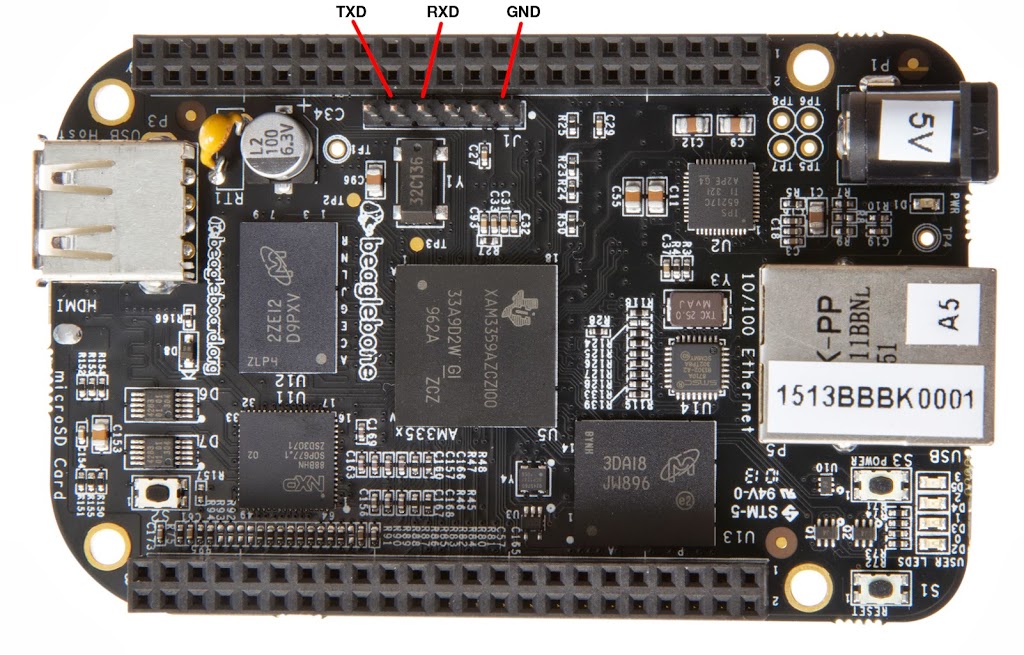
Now that the image has been turned into an installer, you may put the microSD card into the Beagle Bone (without power).
If there is a fourth pin, usually red, do not use. We only need input, output, and ground.
sudo screen <devicename> 115200 sudo screen /dev/ttyUSB0 115200 [Example]
#Screen
Using ssh to tunnel to another host, and then executing screen to keep the session persistent.
ssh -p ### -t user@host.com screen -DRO
Using screen with usb to serial adapter
sudo screen /dev/ttyUSB0 115200
Some other common speeds are 9600, 57600, 38400, 19200
——————————————- #next topic
git clone git@gitserver:/srv/git/project.git
#virt-manager stuff
Start defualt
sudo virsh net-start default
Remove bridge
sudo ifconfig virbr0 dow sudo brctl delbr virbr0
List all
sudo virsh net-list --all
#rsync
sudo rsync -avxHAX --progress /sourcefiles/path /backup/path
#next topic
chmod 700 ~/.ssh chmod 644 ~/.ssh/id_rsa.pub chmod 600 ~/.ssh/id_rsa chmod 755 ~/
#next topic
#next topic
— oemb1905 2018/02/16 00:24